When it comes to securing your payment infrastructure, a balanced security approach is a fundamental best practice in the industry. Encryption, tokenization, firewalls for back-office systems and mobile device management (MDM) solutions all play a critical role in preventing data theft — but a purely technology-based strategy isn’t an end-all solution. Employees, from high-level executives to in-store associates, are an essential piece of your tiered security strategy.
As I discussed in my previous blog post, a balanced security approach pulls together and maintains three main elements: technology, process and people. A fine balance between all three is essential for a state of disciplined execution of your payment security strategy. If any of the elements are missing or not taken seriously, the plan doesn’t work. Consider it this way:
- Technology is the baseline defense against potential threats. Attempting to execute a security strategy without technology leaves employees with a frustrating lack of tools to do their job effectively.
- Clear guidelines and procedures help employees know what to do with the technology under all circumstances. Without process, it’s just automated chaos, and defense technology needs to be implemented and used properly according to process for it to be effective; and
- People are needed to operate and interpret the data from security tools; the tools can’t be left in a closet to function on their own. Alienating people from the security plan leaves major holes that would-be data thieves can take advantage of.
Importance of “People” In Payment Security
People are a crucial piece of this balancing act. Take the manufacturing world, for example, where most production lines have a "STOP" button in case of emergency. Every employee working on the floor is empowered and applauded for recognizing problems and halting the line before things get out of control. In the world of information security, things need to work the same way. Starting at the grassroots – your people (employees) need to recognize that they are an integral part of the team protecting your infrastructure — they are your first line of defense against attacks such as social engineering. The challenge most organizations face is that most employees don’t come equipped with the tools to recognize threats and fraud. Social Engineering and human error combine to be the leading first actions in most data breaches. However, with regular training tailored to your employees, businesses can easily avoid this risk.
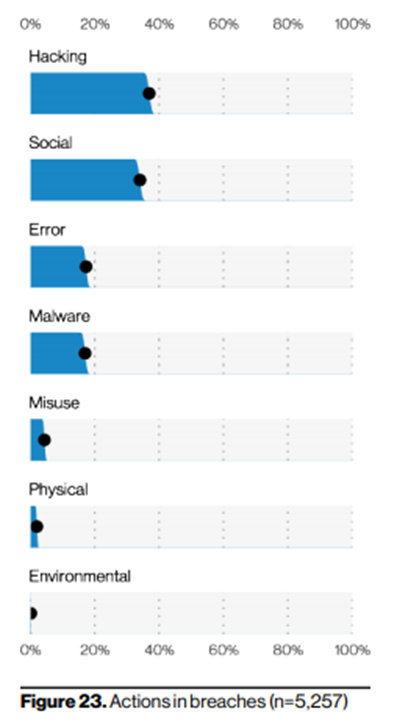
Source: 2021 Verizon Data Breach Incident Report. The figure shows actions in the first step of incidents.
Equipping Your Human Defense
First and foremost, businesses should hire competent, trustworthy and qualified employees. It is easier to teach new technology, procedures and processes to someone with a strong foundation. As a starting point for grassroots security, equip your in-store associates with these six essential best practices:
- Regularly inspect payment acceptance devices (terminals and card readers) for any signs of tampering that can allow cybercriminals to easily capture sensitive data, including credit card information. This can happen in many ways, including adding overlays on terminals when the cashier is not looking, etc.
- Keep an eye out for suspicious behavior in-store; cybercriminals often pose as customers or technicians to gain access to your payment solutions.
- If someone does pose as a technician, be aware of protocols to follow, such as calling your solution provider or manufacturer to confirm any scheduled visits.
- Understand what a safe and secure payment transaction looks like as opposed to a potentially fraudulent one.
- Use unique passwords for every account and don’t share them with other employees. Also, use multi-factor authentication where possible.
- Practice your incident procedure to ensure that everyone knows what to do if you find something suspicious, or something does go wrong. This can work similar to fire drills by taking employees through simulations of different incidents to help them better prepare for the future. Doing these on a regular basis also helps employees be up-to-date on the latest threats and best ways to deal with them.
Fraudsters are constantly evolving and coming up with new ways to steal sensitive data. It is imperative for businesses to keep up with the new developments and better prepare themselves for the future. Your security strategy should be bolstered by a balanced adoption of technology, process and people. Regular training for your employees is a must to ensure they are aware of any new or existing threats in the industry. Preparing them to be a central players in defending against unexpected fraud is an essential part of any well-rounded payment security strategy. If you are looking to learn more about protecting your payment infrastructure from all angles, drop us a line.
Steven Bowles is the Regional Security Officer & Director of Security Solutions at Ingenico










