Don’t Underestimate the Importance of Process in Your Balanced Security Approach
Whether you are a big hospitality chain, a quick-service restaurant or a small retail apparel store, payment security is critical to your business and your reputation. Your customers entrust their payment information to you, and they expect you to protect it.
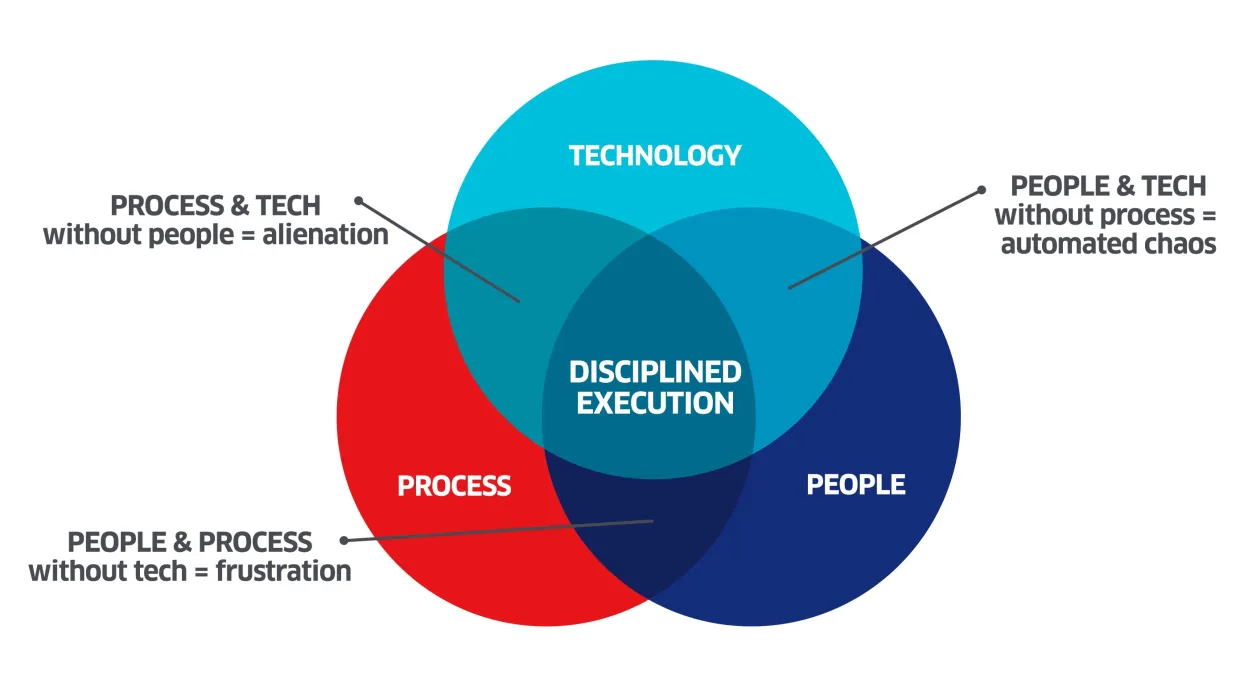
In a previous blog post I talked about how a balanced security approach is a fundamental best practice for payment security. This approach balances three essential components of a security program: technology, people and process.
The technology required for payment security is well understood. Many security solutions exist in the market, from P2PE and tokenization for data protection, to mobile device management (MDM) and security for eCommerce payment platforms.
People are a crucial piece of this balancing act. In my previous post, I discussed how your employees are the front line against such threats as phishing, social engineering and fraud, and how to equip them with the tools they need to spot problems and act accordingly.
The Role of Process in a Balanced Security Approach
A much less commonly discussed component of balanced security is process. At the foundation of your processes is a security governance framework that aims to address the "what" and the "why" of your security program. On top of this are three pillars that address the "how": management systems, best practices and audits.
The Foundation of Process: A Security Governance Framework
The first step in building end-to-end process excellence is to adopt a security governance framework that gives you a blueprint of what to do and why it is necessary to achieve robust security. To do this, you need to have a clear understanding of both your business objectives and the real threats that your organization faces. A framework that is too big will bog you down; a framework that is too light will put you at risk of compromise.
The good news is that you don’t need to start from scratch, because several well-established frameworks exist. The gold standard and foundation of most framework initiatives is the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). With a clear understanding of your business objectives and threats; you can create a "Cybersecurity Profile" that allows you to optimize the CSF to your organization's unique needs.
Within our industry, merchants accepting electronic payments have compliance obligations to follow and meet requirements set out by the Payment Card Industry (PCI) Security Standards Council. This can also act as a framework that can guide you in decisions on how to protect both the confidentiality of your customer's data and your organization from the victim of a breach.
Pillar 1: Management System
Once you have made decisions about your security governance framework, you can establish the management system that will support your security operations. This is a set of policies for executing on the framework, managing security risk, protecting data and limiting the impact of a security breach.
Your management system might address data policies, for example, on whether you will store card data and if so, how you will use it. It will also guide your technology choices, such as how you will protect card and cardholder data while it is in transit (P2PE for example) and at rest (tokenization) and what will be the architecture of your IT environment. The management system should also define how you will measure the success of your security program.
Most importantly, it will answer such “people” questions as:
- Who is responsible for management oversight?
- Who is responsible for the execution of policies?
- Who takes care of day-to-day operations?
- Are all roles and responsibilities appropriate and clearly articulated?
Pillar 2: Best Practices
Once you have documented all the policies in your management system, you will then have to establish a set of day-to-day operational procedures and best practices that are consistent and interoperable across your organization. These are important to have, whether you are replicating processes and behaviors across a global network of big-box outlets, or documenting what the three employees in your retail store should do when presented with a suspicious transaction.
Documented procedures and best practices give you consistency in your service delivery, a baseline that you can use for continuous improvement, a script to follow when things get hectic, and protection during times of change (whether dealing with disaster recovery, adopting new technology or integrating new people).
They also provide the benchmark against which you will measure your own performance in the next process pillar, audits.
Pillar 3: Audits
Through the audit process you can: evaluate your performance, identify areas where you aren’t meeting your security goals, and look for opportunities to improve. Your audit should answer such questions as:
- Are we following the best practices in our day-to-day operations?
- Do employees understand the parts of the governance framework and management system that are pertinent to their roles?
- Does everyone know what they are supposed to do in the event of a data breach?
Reaching PCI compliance can become the focus of such audits, but the reality is that merchants often take in other personal information from customers (e.g., driver's license numbers, government ID numbers, etc.) that is due to the same level of protection. For merchants of all sizes, the audit should enable you to answer that ever-critical question, “Are we protecting our customers' data and our business?”
Finding the Balance
Though this blog has been focused on Process, all three components must be in place to achieve a balanced approach to security. If you neglect one element; chaos, alienation and frustration can reign. In my next blog on balanced security, we’ll take a deeper dive into what can go wrong if one element is missing. In the meantime, if you are looking for a better understanding of how to set up a robust security infrastructure for your organization, get in touch with us and talk to our experts.
Steven Bowles is the Regional Security Officer & Director of Security Solutions at Ingenico Group, North America









